Dissecting a virtual world phishing attack
An interesting development in the latest cybercrime trends has been a marked increase in attacks against online games and virtual worlds, as I have posted previously. One element that I have missed in the discussion about game hacking has been the methods with which cyber-criminals obtain login details and passwords in order to empty the virtual coffers of gamers around the world. I had generally assumed that hackers obtained passwords through a combination of means, including keylogger software, social hacking, guesswork and bad security on the part of the user. I was not aware of large-scale phishing attacks, so when I received my first WoW phishing message, I was both taken aback by its realism, and also in awe of how many people must be falling for this.
First some background. Last year I opened a US World of Warcraft account for occasionally playing when I am back in Costa Rica. I generally do not use this account, so it would be ripe for hijacking. Yesterday I received this message from what looked like a legitimate Blizzard account. I will reproduce it in its entirety only removing the actual link for obvious reasons:
------------------
Subject: Blizzard Account Administration------------
From: Blizzard [donotreply@blizzard.com]
Reply-To: Blizzard [donotreply@blizzard.com]
Greetings,
An investigation of your World of Warcraft account has found strong evidence that the account in question is being sold or traded. As you may not be aware of, this conflicts with Blizzards EULA under section 4 Paragraph B which can be found here:
WoW -> Legal -> End User License Agreement
And Section 8 of the Terms of Use found here:
WoW -> Legal -> Terms of Use
The investigation will be continued by Blizzard administration to determine the action to be taken against your account. If your account is found violating the EULA and Terms of Use, your account can, and will be suspended/closed/or terminated. In order to keep this from occurring, you should immediately verify that you are the original owner of the account.
To verify your identity please visit the following webpage:
[HTTPS link removed]
Only Account Administration will be able to assist with account retrieval issues. Thank you for your time and attention to this matter, and your continued interest in World of Warcraft.
Sincerely,
Account Administration
Blizzard Entertainment
This was a short and concise message that actually seems plausible, as it arrived to the email account with which my US WoW account is registered. It reads well, with no suspiciously dodgy English or ludicrous made-up names; it also points to the relevant legal documents and articles. Thankfully, I immediately checked the links, and rightly enough, the most important one did not direct to Blizzard, it led to ripside.com, which is a small website hosting service. I visited using Google Chrome (which is new enough not to have developed exploits), and this is what I found:

Which looks exactly like the Blizzard's own account management screen found here. Once I entered some meaningless login and password, I got a large page asking for all sorts of details, including name, address, email, and interestingly, the following:
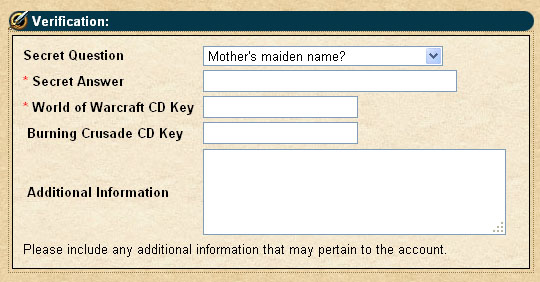
In short, this is all that is needed for anyone to hijack an account, take all the money and items with them, and run. Every guild has stories of members who have been compromised, and from time to time one can hear the desperate cry of a poor sod in Trade chat who shouts "I'VE BEEN HACKED!"
It is important to stress that Blizzard seems to be taking this very seriously, so they have initiated a campaign to make sure users are aware of the security risks involving their account. There is also a procedure in place in order to reinstate money and items to the victims. However, what is not mentioned anywhere is that these actions constitute a crime, and I am concerned that this is precisely the reason why there is such an increase in hacking activities against gamers. As I have mentioned before, there seems to be some reluctance from crime enforcement agencies to respond to cybercrime in general, and game account hacking would seem to be even at the lowest end of priorities. So, a geek had his magic sword stolen? Who cares?
If hackers have moved towards sophisticated phishing attacks, then we are talking about an entirely new level of engagement. Banking phishing sites are usually taken down within hours of the attack through action from anti-phishing organisations. However, the offending site in this specific attack is still up and running 24 hours after the message was received. This seems to indicate that cyber-criminals are catching up to efforts to curb their scams, and are moving to easier pickings in the shape of virtual worlds. The fact is that virtual goods are worth real money, so the temptation for criminals to make some quick earnings through hacking must be the drive behind the growing number of hijacks. While a criminal will certainly get more money from hacking a bank account, it seems that they realise that hacking a virtual world account is less likely to result in prosecution.
The last element in the line of attacks is that according to the email headers, this message came from New Zealand and what appears to be a compromised Hotmail account. Hotmail seems to be a favourite of phishers and spammers, with Youtube videos explaining how to create fake Hotmail accounts.
Much as with bank phishing, there seems to be a toxic triangle that allows some of this to happen. Firstly, email services like Hotmail seem to make it easy for hackers to exploit the system to send fake emails. Secondly, law enforcement and anti-phishing authorities seem unaware and/or uninterested about the phenomenon. Thirdly, users are still falling for many of these attacks due to lack of care and lack of education.
I'm now off to install some anti-keylogger software. I don't want to lose my enchanted knives.

 del.icio.us
del.icio.us




2 comments:
This is great! Thanks so much. Hope it will continue.
you get interesting post about web usability and technology on my blog.Web Usability Blog
Thank you so much for this. I got the same email and was convinced. However, when I got it again, I became wary. Thank you for posting this specific example, confirming my suspisions.
Post a Comment